Describe how Power Platform implements security, including awareness of Common Data Service security roles and Azure Identity Services
Any development environment—even a no-code/low-code one—is subject to abuse by unauthorized users, whether intentional or not. However, because the Power Platform tools are designed for an audience of citizen developers, as well as content consumers, security is a particularly important aspect of their administration. Code-based development environments are not understood by most users, which helps to protect them from casual interference, but they are still subject to deliberate tampering by malicious outsiders. Therefore, the Power Platform tools require security mechanisms like those of any other cloud-based service.
All of the Power Platform tools rely on the Azure Active Directory identity services for user accounts and licensing. Administrators therefore use the standard Azure tools, such as Microsoft 365 admin center, for user account maintenance and license assignment. Apart from this, the main Power Platform tools operate independently, so they each have their own security architecture. The following sections examine the security considerations for each component.
Power BI security
At its most basic, security in Power BI is a matter of sharing content with other users. Developers control access to their content by sharing dashboards, reports, or apps with specific consumers using the interface shown in Figure 1-36. However, for users to access Power BI in the first place, they must first be authenticated and authorized for specific content.
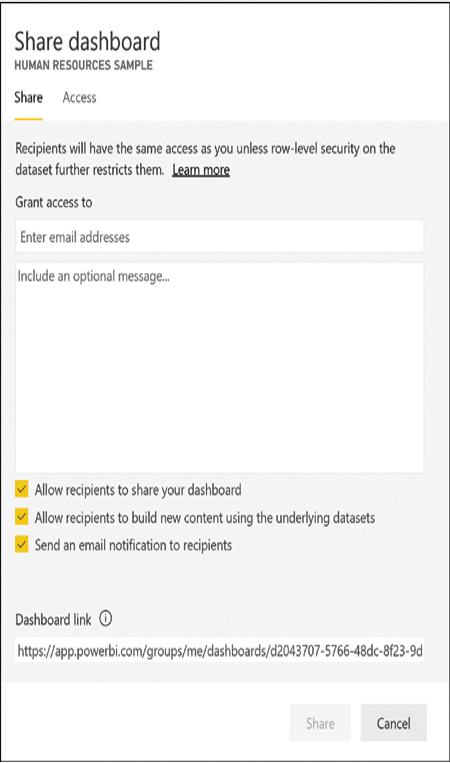
FIGURE 1-36 Power BI Share Dashboard dialog box
Power BI, as implemented in Microsoft Azure, is a service that consists of two clusters: the Web Front End (WFE) cluster and the Back-End cluster, as shown in Figure 1-37.
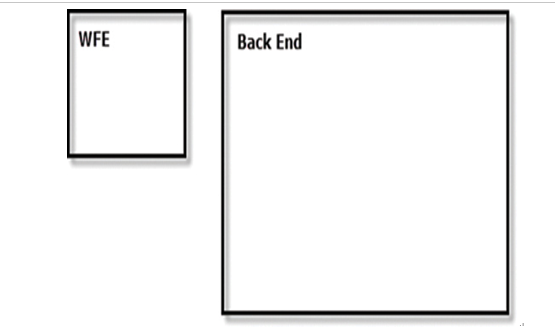
FIGURE 1-37 Power BI clusters architecture
The WFE cluster is responsible for the initial connection by users to the Power BI service and the authentication of the user account, in a process shown in Figure 1-38.
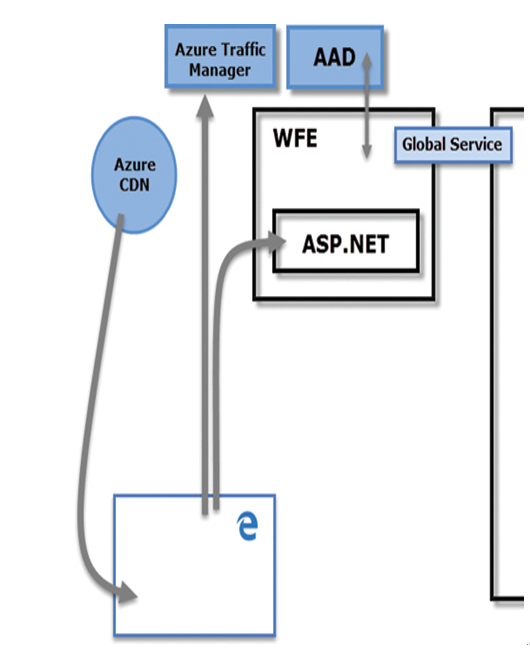
FIGURE 1-38 Browser interaction with the Power BI WFE cluster components
When a user directs a browser to Power BI by typing a URL or clicking a hyperlink, the following procedures occur:
The Azure Traffic Manager (ATM) examines the user’s DNS record and directs the browser connection to the WFE cluster in the nearest Microsoft data center.
The WFE cluster directs the user connection to the Microsoft Online Services login page.
The user is asked to authenticate against its account in Azure Active Directory (AAD). When the authentication is successful, the login page directs the connection back to the WFE cluster.
The WFE cluster authorizes the user’s Power BI service subscription with Azure Active Directory and, if the authorization is successful, obtains an AAD security token.
The WFE cluster consults the Power BI Global Service to determine the location of the correct Back-End cluster for the tenant to which the user belongs.
The WFE cluster directs the user connection to the correct Back-End cluster and supplies the user’s browser with the AAD security token, the address of the Back-End cluster obtained from the Global Service, and information about the current session.
The user’s browser downloads the common files needed to interact with the Power BI service from the WFE cluster and from the Azure Content Delivery Network (CDN). The browser maintains these files for the duration of the session with the Power BI service.
After the authentication and authorization processes are completed successfully by the WFE cluster and the browser downloads the necessary files, all subsequent Power BI communication takes place between the browser and the Back-End cluster directly, without further participation of the WFE cluster.
The Back-End cluster hosts a variety of roles, as well as the data storage media where the Power BI information is stored, as shown in Figure 1-39. The dotted line in the figure represents the division between the modules that are accessible to users via the public internet (on the left) and those that are accessible only indirectly (on the right).
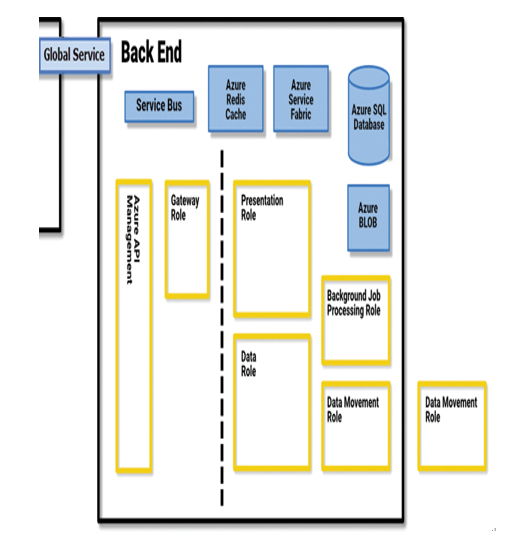
FIGURE 1-39 Power BI Back-End cluster components
The Back-End cluster is responsible for all the Power BI operations for authenticated clients, including the establishment and maintenance of data connections, the creation of the visualizations in dashboards and reports, and the storage of data. Users communicating with the Back-End cluster do so through the Gateway Role.
The Gateway Role and Azure API Management are the only modules accessible to users through the public internet. These modules accept and manage user connections, authorize users for specific content, and then relay all incoming user requests to the other modules in the cluster as needed. For example, a typical transaction in which a user attempts to access a Power BI dashboard, as shown in Figure 1-40, proceeds as follows:
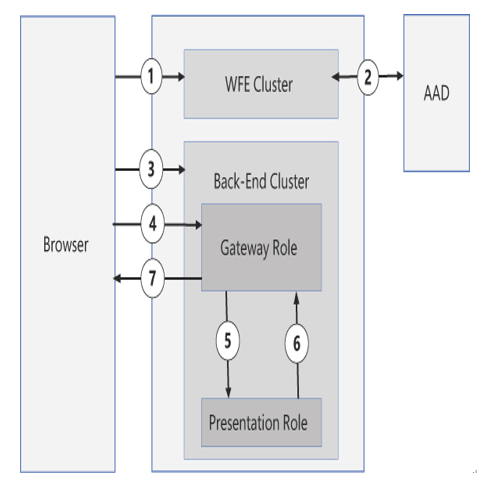
FIGURE 1-40 Power BI transaction
The user’s browser accesses the Power BI portal and connects to the WFE cluster.
The WFE cluster authenticates the user and authorizes the user’s access to Power BI.
The browser connects to the Back-End cluster.
The user generates a request to display a dashboard and sends it to the Gateway Role in the Back-End cluster.
The Gateway Role forwards the request to the Presentation Role, which is responsible for supplying the data needed to create the visualization of the dashboard in the user’s browser.
The Presentation Role sends the requested data to the Gateway Role.
The Gateway Role forwards the data to the user’s browser, and the browser displays the requested dashboard.
Thus, the Presentation Role (and all of the other non-public roles in the Back-End cluster, including the Data Role, the Background Job Processing Role, and the Data Movement Role) are protected from direct internet access by users, both authorized and unauthorized.
