Describe data loss prevention (DLP) policies
The Power Platform tools are designed to access data from outside sources and, in some cases, write data back to those sources. Developers can create canvas apps and flows that access multiple data sources with different sensitivity levels. This process is inherently dangerous because the Power Platform content will eventually be deployed to consumers, who might or might not warrant direct access to sensitive data. Power Platform developers and administrators must exercise control over access to the data sources they use, and one method of doing so is to create data loss prevention policies.
Data loss prevention (DLP) policies are rules, created in the Power Platform admin center, that allow tenant admins and environment admins to classify connectors in three groups, as follows:
■ Non-business—Intended for connectors that access non-sensitive data. Connectors in this group cannot share data with connectors in the Business group. A newly created DLP rule places all connectors in this category by default.
■ Business—Intended for connectors that access sensitive data. Connectors in this group can share data with other connectors only in the Business group; they cannot share data with connectors in the Non-business group.
■ Blocked—Intended for connectors that are not to be used in the environment at all.
To create DLP policies using the wizard in the Power Platform admin center, administrators assign the policy a name and use the interface shown in Figure 1-58 to move selected connectors from the Non-business group to the Business or Blocked group.
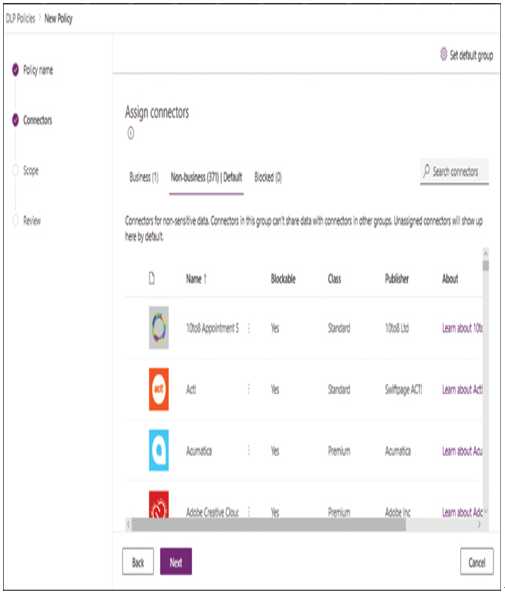
FIGURE 1-58 The Assign connectors page in the New Policy wizard
Then, using scope options, administrators can apply the new DLP policy to an entire tenancy or to specific environments within the tenancy.
Describe how the platform supports privacy and accessibility guidelines
In any service or application that stores data that is potentially sensitive, and especially in cloud-based applications and services, there might be statutes and standards to which the organization must comply, whether because of contracted terms, company policies, or governmental requirements.
Microsoft is aware of these compliance issues and has created a central storehouse for information about them called the Service Trust Portal (STP). STP is a website that is available to everyone at servicetrust.microsoft.com, although some parts of the site are restricted to registered users of Microsoft 365 and other products. Among the many resources on the site are links to documents in the following categories:
■ Audit Reports—Provides independent audit and assessment reports of Microsoft’s cloud services, evaluating their compliance with standards such as those published by the International Organization for Standardization (ISO), Service Organization Controls (SOC), National Institute of Standards and Technology (NIST), Federal Risk and Authorization Management Program (FedRAMP), and General Data Protection Regulation (GDPR)
■ Documents & Resources—Consists of a large library of documents, including white papers, FAQs, compliance guides, penetration test reports, Azure security and compliance blueprints, and other data protection resources
■ Compliance Manager—A risk assessment tool that assesses and scores an organization’s regulatory compliance, based on multiple published standards
■ Industries & Regions—Provides documents containing compliance information for specific industries, such as education, financial services, government, health care, manufacturing, and retail, and specific countries, including Australia, Czech Republic, Germany, Poland, Romania, Spain, and the United Kingdom
■ Trust Center—Links to the Trust Center site, which provides documentation on the means by which Microsoft supports security, privacy, compliance, and transparency in its cloud services
